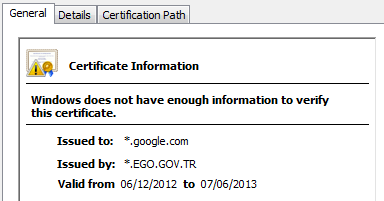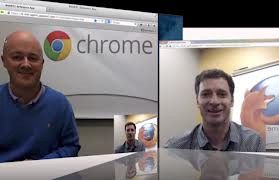
Why the WebRTC video codec choice is important
Real time peer to peer communication on the web has had a good couple of months. At the end of January Chrome and Firefox demonstrated interop of two independent WebRTC implementations and then a couple of weeks ago Google squelched the MPEG LA attack on the open status of it’